Nginx作为WEB容器已经是一个主流的标配了,本文带大家手把手搭建,企业级WEB应用防火墙,目前阿里云WEB防火墙最低价,一个月5000,所以知识就是财富。
- 系统环境:Ubuntu18.04
- WEB容器:Nginx1.9(或更高)
- WAF组建:Modsecurity3.0

owasp top10网络安全入门到放肆
作者 ailx10
会员专享¥19.99
或许Nginx1.9这个版本有点历史久远了,但是是入门学习Nginx的一个好的选择。或许Modsecurity不是好的选择,不过也没关系,纯粹学习的态度,期望打通完整的架构。历史是一面镜子,也是一本深刻的教科书。加油!go!
2019.9.2 21:00测试,平均下载速度8M/s
- 第二步:编译动态库
$ cd /home/modsec
$ git clone https://github.com/SpiderLabs/ModSecurity
$ cd ModSecurity
$ git checkout -b v3/master origin/v3/master
$ sh build.sh
$ git submodule init
$ git submodule update
$ ./configure
$ make
$ make install- 第三步:编译Nginx
$ cd /home/modsec
$ git clone https://github.com/SpiderLabs/ModSecurity-nginx.git modsecurity-nginx
$ wget http://nginx.org/download/nginx-1.9.2.tar.gz
$ tar xzvf nginx-1.9.2.tar.gz
$ cd nginx-1.9.2
$ ./configure --add-module=/home/modsec/modsecurity-nginx
$ make
$ make && make install- 第四步:下载规则集,移动到Nginx配置文件中
$ cd /home/modsec
$ git clone https://github.com/SpiderLabs/owasp-modsecurity-crs.git
$ cp -a owasp-modsecurity-crs /usr/local/nginx/conf/
$ cd /usr/local/nginx/conf/owasp-modsecurity-crs
$ cp crs-setup.conf.example crs-setup.conf
$ sed -ie 's/SecDefaultAction "phase:1,log,auditlog,pass"/#SecDefaultAction "phase:1,log,auditlog,pass"/g' crs-setup.conf
$ sed -ie 's/SecDefaultAction "phase:2,log,auditlog,pass"/#SecDefaultAction "phase:2,log,auditlog,pass"/g' crs-setup.conf
$ sed -ie 's/#.*SecDefaultAction "phase:1,log,auditlog,deny,status:403"/SecDefaultAction "phase:1,log,auditlog,deny,status:403"/g' crs-setup.conf
$ sed -ie 's/# SecDefaultAction "phase:2,log,auditlog,deny,status:403"/SecDefaultAction "phase:2,log,auditlog,deny,status:403"/g' crs-setup.conf- 第五步:将Modsecurity的配置文件,移动到Nginx配置文件中
$ cd /home/modsec/ModSecurity
$ cp modsecurity.conf-recommended modsecurity.conf
$ vim /usr/local/nginx/conf/modsecurity.conf
SecRuleEngine On
$ cp modsecurity.conf /usr/local/nginx/conf/modsecurity.conf
$ cp unicode.mapping /usr/local/nginx/conf/- 第六步:在Nginx配置文件中,创建modsec_includes.conf
$ cd /usr/local/nginx/conf/owasp-modsecurity-crs
$ cp rules/*.data /usr/local/nginx/conf
$ vim /usr/local/nginx/conf/modsec_includes.conf
include modsecurity.conf
include owasp-modsecurity-crs/crs-setup.conf
include owasp-modsecurity-crs/rules/REQUEST-901-INITIALIZATION.conf
Include owasp-modsecurity-crs/rules/REQUEST-903.9002-WORDPRESS-EXCLUSION-RULES.conf
include owasp-modsecurity-crs/rules/REQUEST-905-COMMON-EXCEPTIONS.conf
include owasp-modsecurity-crs/rules/REQUEST-910-IP-REPUTATION.conf
include owasp-modsecurity-crs/rules/REQUEST-911-METHOD-ENFORCEMENT.conf
include owasp-modsecurity-crs/rules/REQUEST-912-DOS-PROTECTION.conf
include owasp-modsecurity-crs/rules/REQUEST-913-SCANNER-DETECTION.conf
include owasp-modsecurity-crs/rules/REQUEST-920-PROTOCOL-ENFORCEMENT.conf
include owasp-modsecurity-crs/rules/REQUEST-921-PROTOCOL-ATTACK.conf
include owasp-modsecurity-crs/rules/REQUEST-930-APPLICATION-ATTACK-LFI.conf
include owasp-modsecurity-crs/rules/REQUEST-931-APPLICATION-ATTACK-RFI.conf
include owasp-modsecurity-crs/rules/REQUEST-932-APPLICATION-ATTACK-RCE.conf
include owasp-modsecurity-crs/rules/REQUEST-933-APPLICATION-ATTACK-PHP.conf
include owasp-modsecurity-crs/rules/REQUEST-941-APPLICATION-ATTACK-XSS.conf
include owasp-modsecurity-crs/rules/REQUEST-942-APPLICATION-ATTACK-SQLI.conf
include owasp-modsecurity-crs/rules/REQUEST-943-APPLICATION-ATTACK-SESSION-FIXATION.conf
include owasp-modsecurity-crs/rules/REQUEST-949-BLOCKING-EVALUATION.conf
include owasp-modsecurity-crs/rules/RESPONSE-950-DATA-LEAKAGES.conf
include owasp-modsecurity-crs/rules/RESPONSE-951-DATA-LEAKAGES-SQL.conf
include owasp-modsecurity-crs/rules/RESPONSE-952-DATA-LEAKAGES-JAVA.conf
include owasp-modsecurity-crs/rules/RESPONSE-953-DATA-LEAKAGES-PHP.conf
include owasp-modsecurity-crs/rules/RESPONSE-954-DATA-LEAKAGES-IIS.conf
include owasp-modsecurity-crs/rules/RESPONSE-959-BLOCKING-EVALUATION.conf
include owasp-modsecurity-crs/rules/RESPONSE-980-CORRELATION.conf- 第七步:修改Nginx配置文件nginx.conf
$ vim /usr/local/nginx/conf/nginx.conf
server {
listen 80;
server_name localhost;
#charset koi8-r;
#access_log logs/host.access.log main;
location / {
modsecurity on;
modsecurity_rules_file /usr/local/nginx/conf/modsec_includes.conf;
root html;
index index.html index.htm;
}
...
}- 第八步:验证配置文件是否正确
$ /usr/local/nginx/sbin/nginx -t
nginx: the configuration file /usr/local/nginx/conf/nginx.conf syntax is ok
nginx: configuration file /usr/local/nginx/conf/nginx.conf test is successful- 第九步:启动Nginx
$ /usr/local/nginx/sbin/nginx -c /usr/local/nginx/conf/nginx.conf- 第十步:验证正常访问

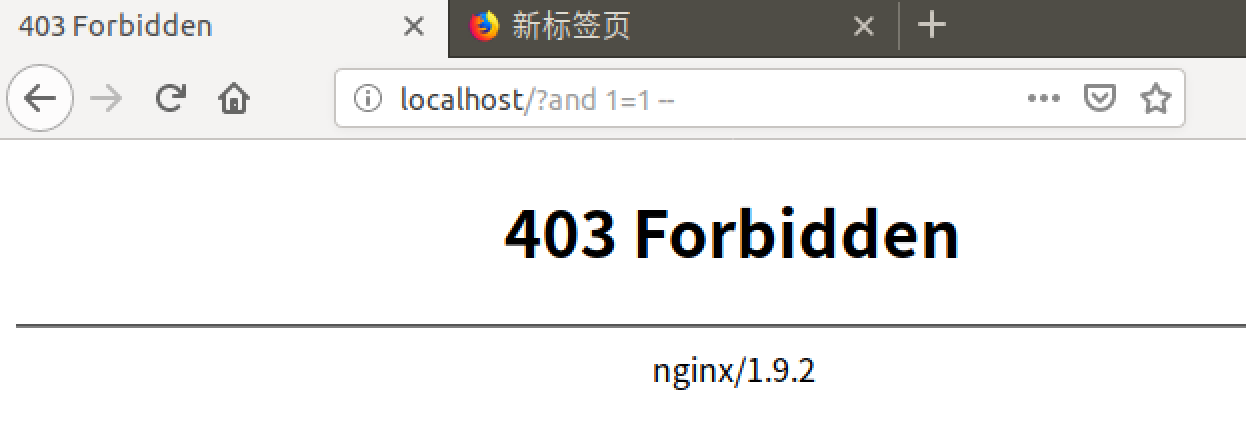
- 第十一步:验证异常访问
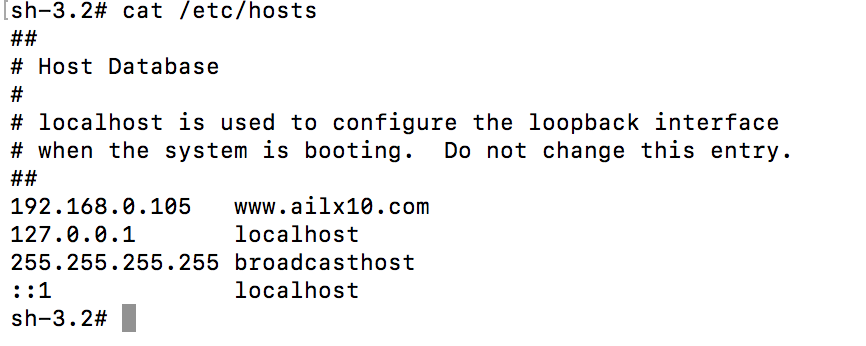
配置本地域名如下:
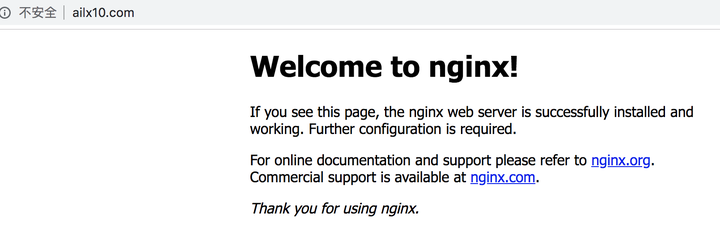
本地访问虚拟机中的Nginx:
参考
- ^ModSecurity https://github.com/SpiderLabs/ModSecurity
- ^利用 ModSecurity 在 Nginx 上构建 WAF https://www.hi-linux.com/posts/45920.html

